Computers tips
The biggest problem users have with their computers is their little
knowledge of how to secure and protect their personal computers and
their information.
Computer tip number one for every
user is to use an anti-virus program. Most use an anti-virus program
already installed on their computer but like most some have no
anti-virus installed at all.
What most users don’t know is that there are free programs available
that work just as great if not better than paid versions. Protecting
your computer is the 1st step that should be taken when using your
computer. Knowing how to update the anti-virus program is 2nd. Malware,
Trojans, spyware and many other types can render your pc or laptop
useless, and may even make it vulnerable for hackers to steal bank
information, passwords and other private data needed for identity theft.

Computers tips
Some
computers tips the users can do themselves to
help secure their data are to learn about safe –browsing. By using a
program like WOT, you can browse sites knowing it’s a safe site to
visit. It gives you a rating and warns you if it’s a potentially harmful
site. Another computer tip is to know how to update your browser.
Updates are readily available by going to the site of the browser and
checking for new updates.
One of the most important of all the computers tips is to use a
firewall. Windows has a build in firewall or you can use free programs
as an added protection. User should also be wary of downloading files
over the internet. Never download from site you don’t know, if you have
question about the site use Google to search the site. Educating
yourself and having good computer habits will reduce your stress and
prolong the life of your computer.
Backing up your computer to an external hardrive will reduce the risk
of losing precious date should your computer become infected or your
hard drive fails you. These basic steps will help but so will making
sure to password protect logons, bank accounts, even your pc. Using a
strong password will make it harder for hackers to crack and keep you
and your computer safe.
Computer Tips for New Users
In today’s tech savvy, electronic age, almost everyone has a laptop
or home computer. We all know how to check e-mail, chat and use Facebook
or tweet on twitter. But, the key to keeping your new gadget alive,
well secure and clean is a little less known to the everyday user. So,
to help keep your life simple, here are a few computer tips that just
might save you from having to pay someone to fix the electrical beast or
worse yet, pay someone to fix something that you think is broken.
Let’s talk about a few things that you should know, no matter what
stage of user you are, from beginner to power user, these computer tips
and descriptions should help you learn how to resolve the issues
associated with them. First a “Cookie”, is a file that a web page stores
on your computer. It allows the web page and therefore the company to
remember what you looked at, what you purchased and even keeps track of
things like page layout, etc. This can be good, but can also be used
negatively by questionable companies. It is stored on your computer and
should be cleaned often.

Computer Tips for New Computer Users
It is up to you to keep your gadget clean. “Malware”, is simply a
piece of software usually, accidentally installed by the user that can
cause malicious intent, like switching your home page in your web
browser or sending your search engine to another default engine. It is
sometimes packaged with a piece of software that is downloaded from the
internet and is installed without the users knowledge.
Remember this computer tip: It is best to always get software form a
reputable source and refrain from clicking or downloading on links that
can cause malicious intent. “Spyware”, is a little worse than malware,
it can be installed the same way as malware, but can also attack your
computer by just visiting a web page or by viewing an infected image.
It’s important to watch your step; in as much if you were in a seedy
part of town you might not go down an alley or walk alone into a darkly
lit store.
Computer Tip : how to clean, speed and improve your PC performance
By using very easy methods, you can improve your computer and
increase your PC speed, also keep it running smoothly. You can use
various tools available in the all versions of the Windows operating
systems like windows vista, windows 7 and windows XP to maintain your PC
and make your PC clean, faster and safe. Some of the simple computer
tips and guidelines are as follows to make your computer faster and
teach you to improve your computer’s performance and efficiency.
First of all install and update a good antivirus to help and protect
your computer from spyware, malwares and viruses. This is the one
important cause which makes your PC slow and decreases the efficiency of
your computer. The most important computer tip is to upgrade the RAM
and also includes use of three important tools Check Disk, Disk
Defragmenter, and Disk Cleanup. Every Windows operating system
facilitates these three important tools to help keep your computer run
smoothly. You can run Check Disk and Disk Defragmenter to check, detect,
repair and clean disk errors of your computer.
Disk Defragmenter scans the hard drive for bad sectors, errors and
helps prevent data loss. And if your hard disk is full or have a very
little space on it than do backup of your important documents and run
Disk Cleanup to clean unused and unnecessary files. Disk clean up will
removes all unnecessary and unused files from your computer. Disk Clean
up will help you to remove unused files, unnecessary and unwanted
programs, empty the recycle bin, remove error reports and temporary
files, and Remove unused restore points. You should also remove your
temporary files and cookies from your computer because these temporary
files use lots of space and can slow your computer’s speed and
performance.
By performing all these simple computer tips and steps monthly you
can find it easier to improve your computer speed, performance and
efficiency.














 Features of System Software are following
Features of System Software are following Features of Application Software are following
Features of Application Software are following














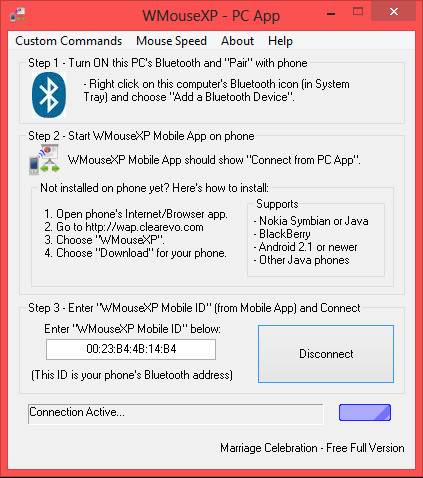

![sshot-2010-05-28-[13-09-22]](http://cdn.howtogeek.com/wp-content/uploads/2010/05/sshot20100528130922.png)











